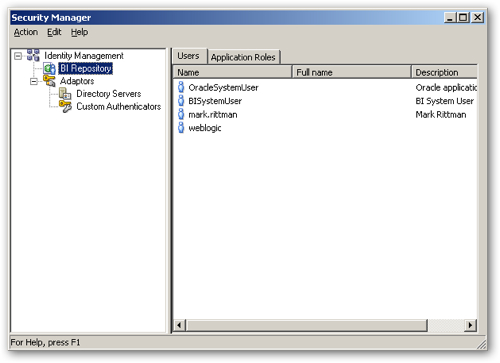
OBIEE 11gR1 Security Explained : An 11g Security Overview
If you're evaluating OBIEE 11g and working through the long list of new features, one of the topics that's potentially most confusing is the new security setup. Whilst basic concepts such as object-level and data-level security are the same in 11g as in 10g, Oracle Fusion Middleware now comes into the picture and security is now much more aligned with the rest of the Oracle middleware stack. So what are the important things to know, how do we now administer users and groups, and how do we perform tasks such as linking security to Microsoft Active Directory?
As a starting point, let's have a think about what we mean by security, and what tasks we want to manage as part of security. How about:
- Users logging in and out
- Lists of users and groups
- Connections through to external directories containing lists of users, groups and password
- Administration of all of this
- Application roles, and rights and permissions we assign to these roles
- Permissions on BI objects (subject areas, tables, columns, reports, dashboards etc)
- Permissions to use features such as Answers, Actions, Briefing Books and so on
- Being able to report against, and audit, security settings
- Authentication - checking passwords and other tokens against user lists, to "authenticate" a user and check that they are who they say they are
- Authorization - once we know who they are, what are we going to "authorize" them to do on our system.
- Administration - how do we administer these lists of users, groups and permissions, plus connections to external directories and applications
OBIEE Security Providers
So, where do we start with all this? Well, to take OBIEE 11g as a whole, this new releases relies on three "security providers":
- An Authentication Provider, that provides the list of users and groups and authenticates their passwords. In 11g, by default this is provided by the WebLogic Server LDAP Server, but you can change it to use Microsoft Active Directory, Oracle Internet Directory or other third-party directory servers.
- A Policy Store Provider, again by default set to WebLogic Server, that provides a list of Application Roles and Application Policies. It's these that are used in 11g to provide access to BI objects in the RPD and webcat, and provide access to tasks such as browse the RPD or execute agents.
- A Credential Store Provider, used for storing securely passwords and user details that are needed to secure interactions between components such as the BI Presentation Server and the Action Framework. In 10g, you used the credstore and cryptotools for this, in 11g it's built into OPSS and WLS.
The diagram below shows a schematic for Oracle Platform Security Services:
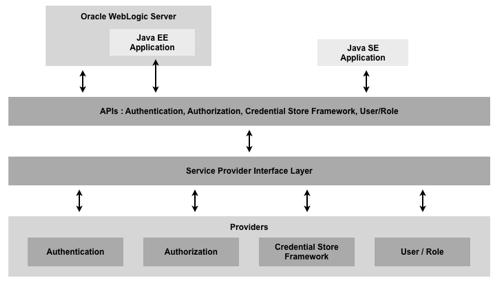
- An Identity Store (by default, the WLS LDAP Server) contains the list of users and groups accessing your system
- A Policy Store contains the list of application roles, and application policies, specifying who can do what (fairly granular for java components, high-level for system components)
- A Credential Store contains securely stored usernames and passwords used for inter-application authentication
- All of the above can be handled internally in WLS, or "outsourced" to directories such as AD or OID
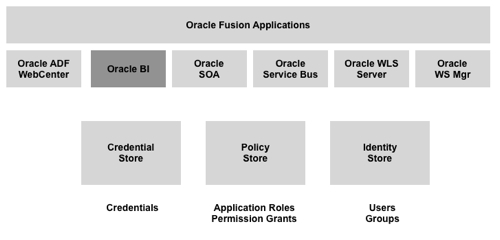
- Application Roles are the FMW11g way that we group sets of permissions which are then granted to users or groups
- Application Policies are the sets of permissions assigned to application roles
- The Embedded WLS LDAP Server replaces the list of users and groups in the 10g RPD
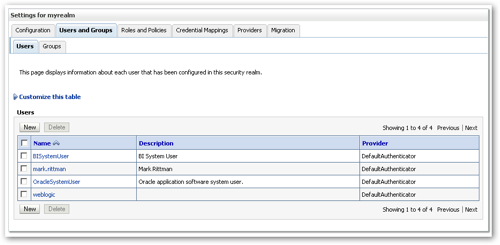
This addresses the requirement for an authentication provider, and the default configuration also provides a default policy store provider, which is accessed through Fusion Middleware Control and allows us to create and maintain application roles, assign policies to the roles and then map our LDAP groups to these roles.
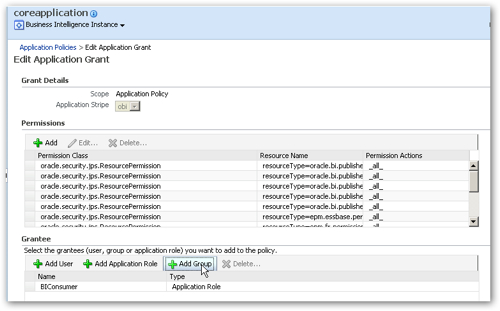
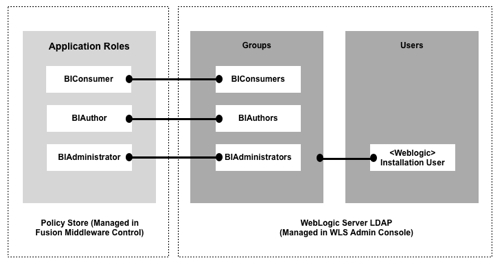
Application roles and policies are I guess the big new thing in OBIEE 11g security. Instead of defining security in terms of groups in the RPD or an LDAP server, OBIEE 11g uses a role-based approach to which permissions and privileges are assigned. Application roles represent a functional role (such as Marketing Analyst, Northern User) which a user has, which gives them the privileges to do that role. Creating this abstraction layer away from the physical groups that are found in an LDAP server gives you a number of advantages:
- You don't have to grant BI access permissions based on whatever groups just happen to be your LDAP server,
- or more likely, find these are irrelevant to BI and therefore you have to roll-your-own groups, typically held externally in a set of database tables
- Also, you can bundle up these application roles and policies and export them as artifacts between different environments (dev and test, for example)
- Beforehand, you need to review the application roles you've got, and potentially create more appropriate ones that make use of the shipped application policies (to create webcat admins, for example, who can't then go on to edit the RPD)
- Either create your users and group in the WLS LDAP Server, or add a new authentication provider (and possibly, policy store provider and credential store provider) to connect to the users and groups in your corporate directory
- Create mapping between your LDAP groups and your application roles, typically granting application roles to your LDAP groups
- Manually add users to other application roles you've created, if your LDAP server doesn't have appropriate or granular-enough groups
- Go to the BI Administration tool and use these application roles to grant access to subject areas, and associate row-level filters to these roles
- Go to the BI Presentation Server admin screen and grant permissions on BI objects, and on BI Presentation Server functionality, to these roles