Oracle BI EE 11g - Security Auditing - Web Catalog Security
BI EE Web Catalog security is an area that generally requires a lot of understanding especially while migrating Web Catalogs. There is not a lot available in the documentation that goes into detail on how .ATR files store security. Its a known fact that doing a file system copy of reports and dashboards from one web catalog to another can potentially corrupt the security. But unless we know how .ATR files store the security, it will be very difficult to know how corruption can happen just by doing a file system copy. This is what i covered as part of my Open World Presentation yesterday. You can download the full set of slides from here. I will quickly go through the important parts of the presentation here.
Binary Representation of Web Catalog Permissions:
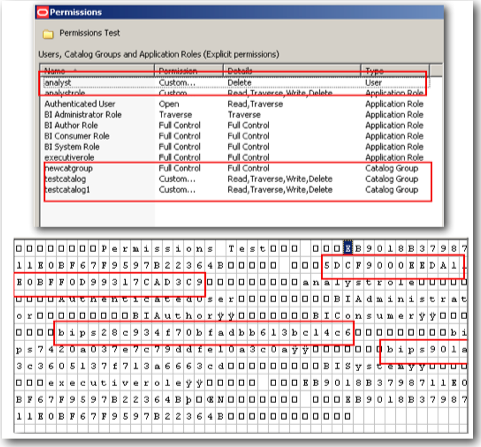
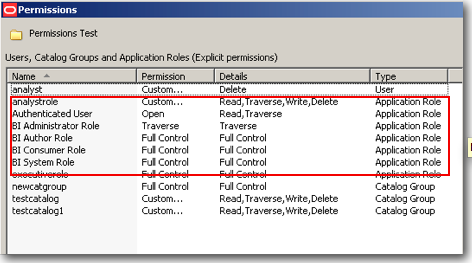
In BI EE web catalog we can assign quite a lot of permissions(shown below) for each user/role. Its important to understand how the permissions are represented internally. BI EE follows a binary representation (similar to the unix folder permissions - 777,775 etc). BI EE uses a total of 16 bits to represent the Access Control List (basically the permissions) as shown below
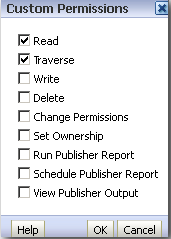
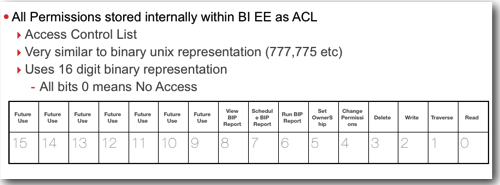
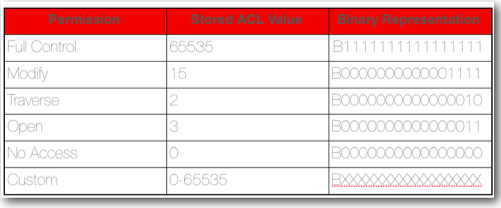
While assigning users/roles to a catalog object, they are stored internally in a binary format. The screenshot below shows how they are actually stored.
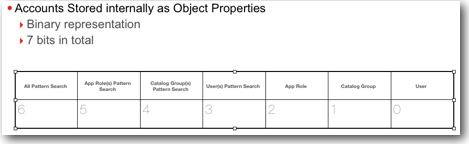
Decompiling .ATR files:
As i mentioned above, all the accounts, their corresponding permissions that are relevant to a catalog object are stored within the .ATR file. The above binary representation is also stored in the byte code of the .ATR file. But we need to know how to interpret the file and look at the contents without opening up catalog manager.
Understanding Application Role & Permissions Storage:
While assigning permissions to an application role on a catalog object, both the permission and the account get pushed inside the .ATR file. So to understand how they are stored internally lets open up the .ATR file of a sample folder called Permissions Test in a HEX editor.
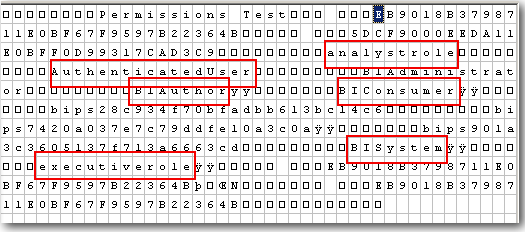
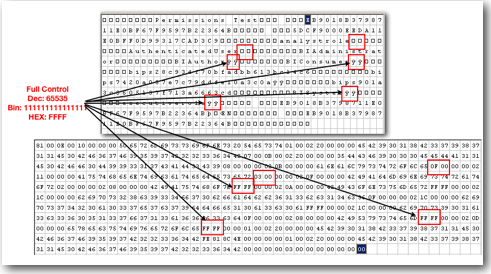
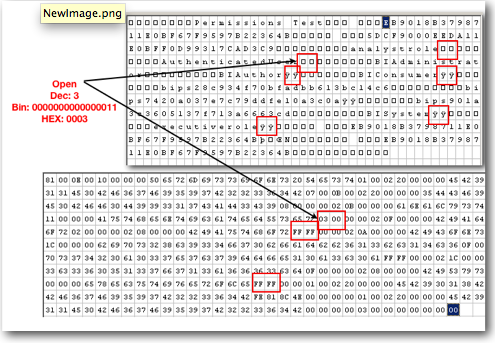
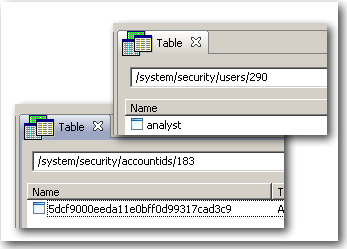
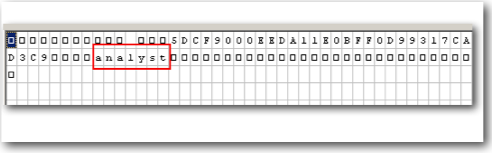
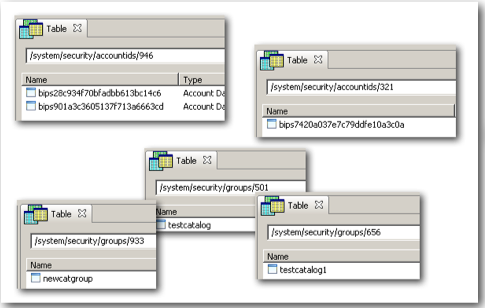
Unlike Application Roles which are stored in ASCII format, users and web catalog groups are stored in an encrypted format. So, it is not straightforward to understand how they are stored internally.