Oracle BI EE 11g – Security Integration with Microsoft Active Directory
As Mark had mentioned here, one big change in BI EE 11g is the adoption of OPSS or Oracle Platform Services Security Model as a framework for security in BI EE. In BI EE 10g, integration with external LDAP security had to be done through the use of Init Blocks and LDAP Servers setup within the repository. In BI EE 11g, the older method of integration is still supported and will work. But the recommended approach is to setup the LDAP as a security provider in Weblogic. In today's blog post, we shall see how to go about setting up Active Directory as a security provider in Weblogic.
When we install BI EE 11g, a Default Security provider is configured out of the box. So, any new user/group that we add to the Default Security Provider can be assigned to Application Roles directly. To change the Default Security Provider to an Active Directory Provider we will have to follow the steps outlined below.
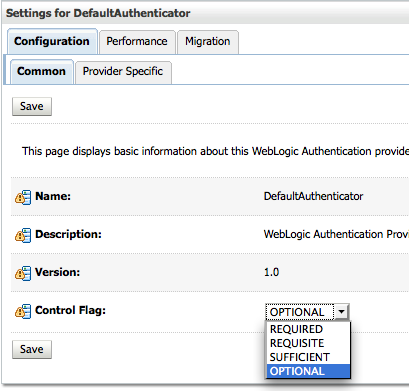
First step is to make sure that we are changing the Control Flag property of the Default Security provider from SUFFICIENT to OPTIONAL. This step ensures that we can have users coming in from other Providers as well. This is done from the Admin Console (http://localhost:7001/console)
 After this, the next step is to add a provider to Weblogic to connect to the Active Directory instance. This step requires us to know 4 main Active Directory Properties
After this, the next step is to add a provider to Weblogic to connect to the Active Directory instance. This step requires us to know 4 main Active Directory Properties
1. Base DN - The base path from where the LDAP search will happen (for users & groups) 2. Bind DN/Principal - This is the Active Directory Administrator user DN that has the privileges to get all the users/groups from the Base DN. Also the password for this user will be required. 3. Active Directory ServerName & Port 4. User Attribute - This attribute is what will be extracted as the username for the users residing in Active Directory. For AD, the attribute name will be sAMAccountName.
Before making any change in Weblogic, ensure that you have all the properties identified correctly. To ensure whether we have got all the properties correctly, there are a couple of methods.
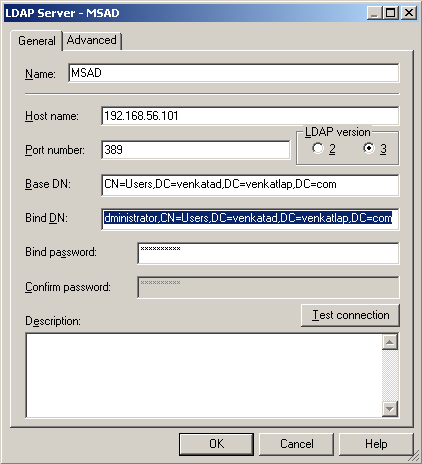
1. In the first method, create a dummy LDAP server connection to Active Directory using the traditional 10g method. This will help us in validating the connection. In my case, the properties that i have are
Base DN: CN=Users,DC=venkatad,DC=venkatlap,DC=com Bind DN: CN=Administrator,CN=Users,DC=venkatad,DC=venkatlap,DC=com AD port: 389 (Default LDAP port without SSL) User Attribute - sAMAccountName (this does not change across instances)
Lets test this out from the LDAP Server setup within the repository.
 When we test this connection, the connection should be successful (there is a bug in this release - Though the connection is successful it will show a wrong icon but with the correct message).
When we test this connection, the connection should be successful (there is a bug in this release - Though the connection is successful it will show a wrong icon but with the correct message).
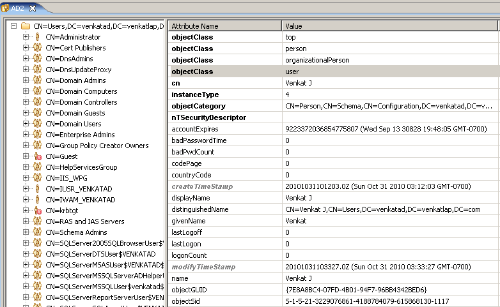
 2. The second method is to use any external LDAP Clients that are available like LDAPSoft etc.
2. The second method is to use any external LDAP Clients that are available like LDAPSoft etc.
 These will basically help us in validating the connection to LDAP. Once we are sure about the properties, lets go into the Admin Console and add a new Provider.
These will basically help us in validating the connection to LDAP. Once we are sure about the properties, lets go into the Admin Console and add a new Provider.
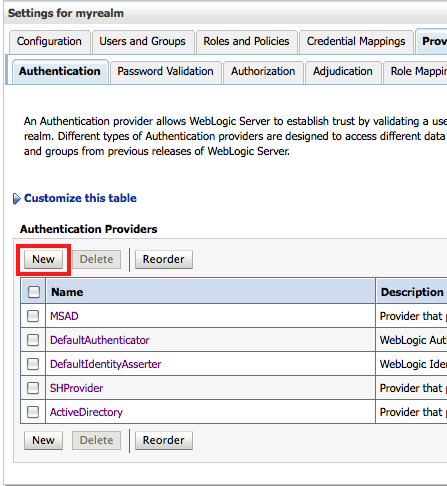 Give it a name like say MSAD. Choose the ActiveDirectoryAuthenticator as the provider type and then provide all the properties that we validated above.
Give it a name like say MSAD. Choose the ActiveDirectoryAuthenticator as the provider type and then provide all the properties that we validated above.
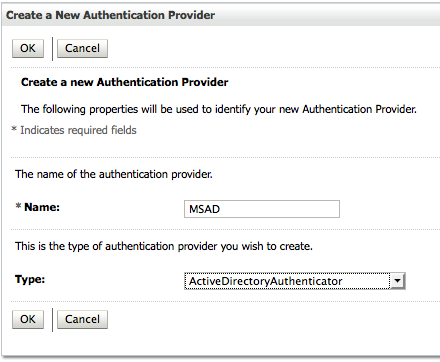
 Principal: CN=Administrator,CN=Users,DC=venkatad,DC=venkatlap,DC=com
Password: Administrator password
User Base DN: CN=Users,DC=venkatad,DC=venkatlap,DC=com
Principal: CN=Administrator,CN=Users,DC=venkatad,DC=venkatlap,DC=com
Password: Administrator password
User Base DN: CN=Users,DC=venkatad,DC=venkatlap,DC=com
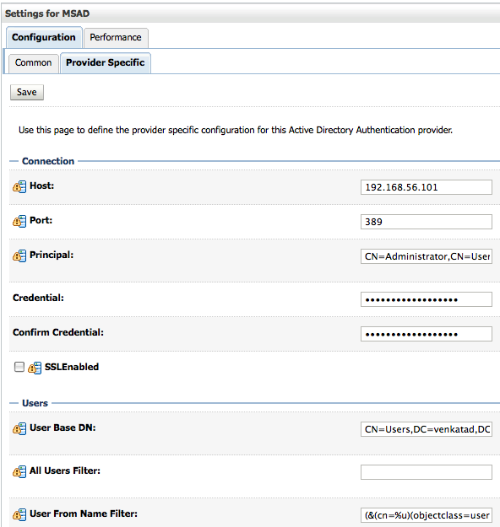
Unlike BI EE 10g, where we did not have a lot of control on how BI EE was actually searching AD, with weblogic we have more control. Also ensure that the User Attribute property points to sAMAccountName as shown below
 After adding this provider, we need to restart the Admin Server. Before making any further change, after the restart we should be starting to see the Users defined in Active Directory to appear in Weblogic Users/Group section. Ensure that you are able to see the users in your instance as well before moving on to the next step.
After adding this provider, we need to restart the Admin Server. Before making any further change, after the restart we should be starting to see the Users defined in Active Directory to appear in Weblogic Users/Group section. Ensure that you are able to see the users in your instance as well before moving on to the next step.
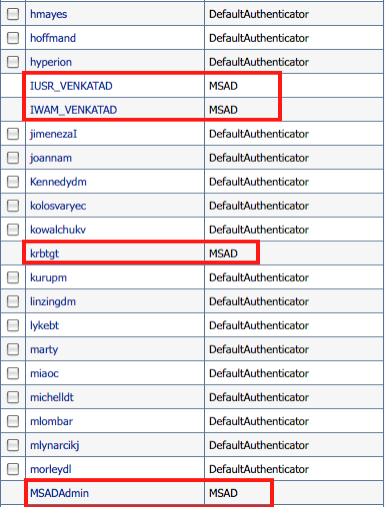 After verifying the connection, the next step is to make Active Directory as the first searchable directory i.e during login as Weblogic can have multiple providers, we need to specify from which provider the search for users/groups will start. This is done through the Reorder button in the Providers tab of the Admin Console. Ensure that the Active Directory Provider we created comes first as the Searchable provider.
After verifying the connection, the next step is to make Active Directory as the first searchable directory i.e during login as Weblogic can have multiple providers, we need to specify from which provider the search for users/groups will start. This is done through the Reorder button in the Providers tab of the Admin Console. Ensure that the Active Directory Provider we created comes first as the Searchable provider.
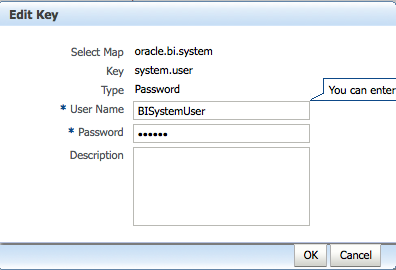
 The next step is to delete the BISystemUser from the Default Provider and then Create it in Active Directory. The reason for doing this is, Credential Store entries of BI EE 11g use the out of the box Configured BISystemUser present in the Default Provider. As our preferred provider now is Active Directory, we will have to make the BISystemUser to be available in Active Directory.
The next step is to delete the BISystemUser from the Default Provider and then Create it in Active Directory. The reason for doing this is, Credential Store entries of BI EE 11g use the out of the box Configured BISystemUser present in the Default Provider. As our preferred provider now is Active Directory, we will have to make the BISystemUser to be available in Active Directory.
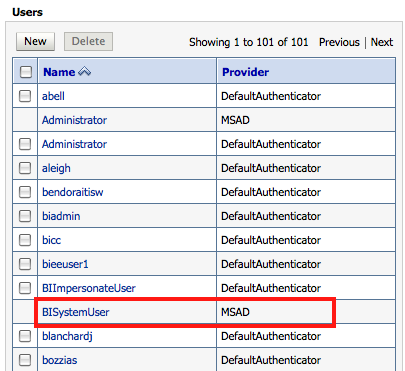 Restart the Admin Server. If you want to use some other name(or a different password) instead of BISystemUser in Active Directory, then the system.user Credential Key will have be updated from Enterprise manager Credential Store (to point to the correct user/password)
Restart the Admin Server. If you want to use some other name(or a different password) instead of BISystemUser in Active Directory, then the system.user Credential Key will have be updated from Enterprise manager Credential Store (to point to the correct user/password)
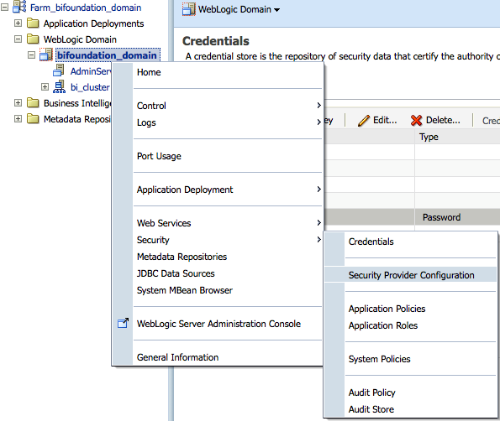
 Even after making these changes, after restarting the Admin Server, you will notice that login to BI EE will fail. The reason for that is we need to configure the Identity Store to basically pick up sAMAccountName property that we have setup in the LDAP. In order to do, we login to Enterprise manager (http://localhost:7001/em) and the expand WebLogic Domain folder as shown below. Right click on the bifoundation_domain and then click on Security > Security Provider Configuration.
Even after making these changes, after restarting the Admin Server, you will notice that login to BI EE will fail. The reason for that is we need to configure the Identity Store to basically pick up sAMAccountName property that we have setup in the LDAP. In order to do, we login to Enterprise manager (http://localhost:7001/em) and the expand WebLogic Domain folder as shown below. Right click on the bifoundation_domain and then click on Security > Security Provider Configuration.
 Click on the Configure button of the Identity Store Provider and add the 2 entries as shown below.
Click on the Configure button of the Identity Store Provider and add the 2 entries as shown below.
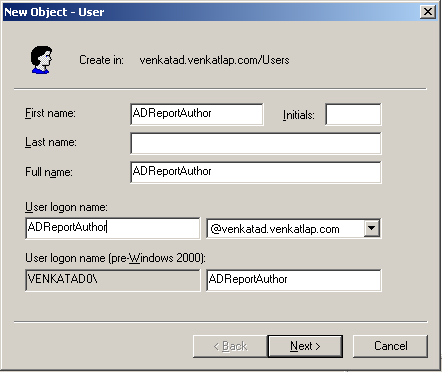
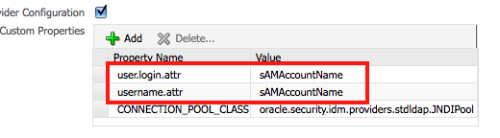 These 2 entries are absolutely needed as they help in propagating the credentials from AD to BI EE. After this change, restart the Managed Server. Lets now add a new user in Active Directory called ADReportAuthor.
These 2 entries are absolutely needed as they help in propagating the credentials from AD to BI EE. After this change, restart the Managed Server. Lets now add a new user in Active Directory called ADReportAuthor.
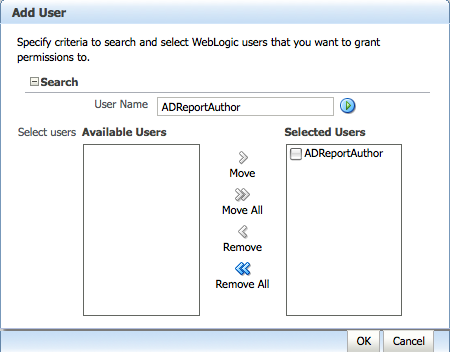
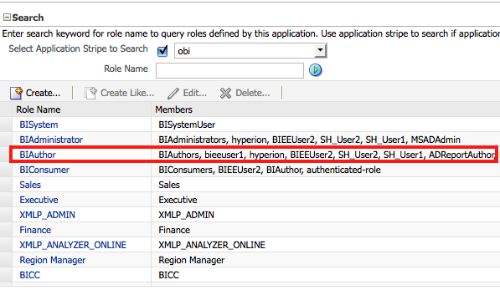
 From Enterprise Manager, lets add this user now to the BIAuthor Application role.
From Enterprise Manager, lets add this user now to the BIAuthor Application role.
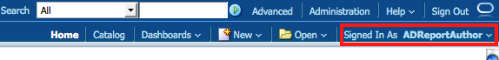
 If we now login to BI EE using the ADReportAuthor, we will be able to do so as weblogic is now configured to connect to AD.
If we now login to BI EE using the ADReportAuthor, we will be able to do so as weblogic is now configured to connect to AD.
 This is a lot easier when compared with setting the security up in 10g. But i believe currently its not supported to have multiple providers (users coming from 2 directories) as the Identity Store attribute setup basically will match only one provider. But it will be good, if BI EE can support multiple providers as well since Weblogic supports it by default.
This is a lot easier when compared with setting the security up in 10g. But i believe currently its not supported to have multiple providers (users coming from 2 directories) as the Identity Store attribute setup basically will match only one provider. But it will be good, if BI EE can support multiple providers as well since Weblogic supports it by default.
Update: After enabling an Active Directory provider, the older weblogic super-user that you had used for logging in to Enterprise Manager or Weblogic Console will continue to work, but it won't now work as a login to BI EE. This behavior is controlled by the Administrators group in the Default Authenticator. Any user in any directory (which is not disabled) when assigned to this group can still log in to EM & Console, but log-in to BI EE is controlled by the Application Roles and authentication provider sequence, and the weblogic user won't be in the new set of AD log-ins and therefore won't have the required application role.