OBIEE Enterprise Security
The Rittman Mead Global Services team have recently been involved in a number of security architecture implementations and produced a security model which meets a diverse set of requirements. Using our experience and standards we have been able to deliver a robust model that addresses the common questions we routinely receive around security, such as :
"Whats considerations do I need to make when exposing Oracle BI to the outside world?"
or
"How can I make a flexible security model which is robust enough to meet the demands of my organisation but easy to maintain?"
The first question is based on a standard enterprise security model where the Oracle BI server is exposed by a web host, enabling SSL and tightening up access security. This request can be complex to achieve but is something that we have implemented many times now.
The second question is much harder to answer, but our experience has led us to develop a multi-dimensional inheritance security model, with numerous clients that has yielded excellent results.
What is a Multi-dimensional Inheritance Security Model?
The wordy title is actually a simple concept that incorporates 5 key areas:
- Easy to setup and maintain
- Flexible
- Durable
- Expandable
- Be consistent throughout the product
While there numerous ways of implementing a security model in Oracle BI, by sticking to the key concepts above, we ensure we get it right. The largest challenge we face in BI is the different types of security required, and all three need to work in harmony:
- Application security
- Content security
- Data security
Understanding the organisation makeup
The first approach is to consider the makeup of a common organisation and build our security around it.
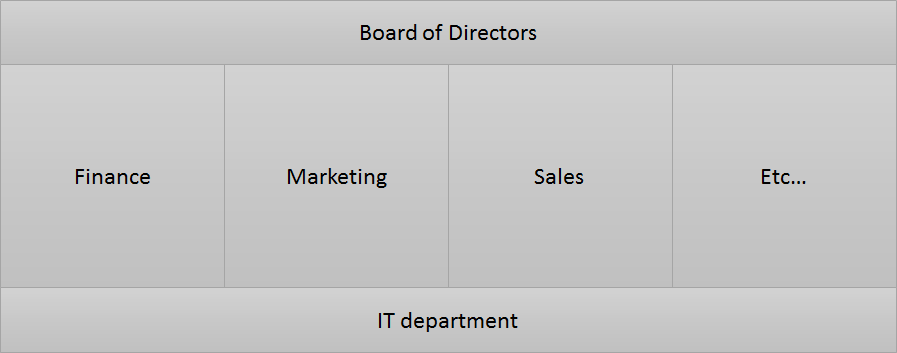
This diagram shows different Departments (Finance, Marketing, Sales) whose data is specific to them, so normally the departmental users should only see their own data that is relevant to them. In contrast the IT department who are developing the system need visibility across all data and so do the Directors.
What types of users do I have?
Next is to consider the types of users we have:
- BI Consumer: This will be the most basic and common user who needs to access the system for information.
- BI Analyst: As an Analyst the user will be expected to generate more bespoke queries and need ways to represent them. They will also need an area to save these reports.
- BI Author: The BI Author will be able to create content and publish that content for the BI Consumers and BI Analysts.
- BI Department Admin: The BI Department Admin will be responsible for permissions for their department as well as act as a focal point user.
- BI Developer: The BI Developer can be thought of as the person(s) who creates models in the RPD and will need additional access to the system for testing of their models. They might also be responsible for delivering Answers Requests or Dashboards in order to ‘Prove’ the model they created.
- BI Administrator: The Administrator will be responsible for the running of the BI system and will have access to every role. Most Administrator Task will not require Skills in SQL/Data Warehouse and is generally separated from the BI Developer role.
The types of users here are a combination of every requirement we have seen and might not be required by every client. The order they are in shows the implied inheritance, so the BI Analyst inherits permissions and privileges from the BI Consumer and so on.
What Types do I need?
Depending on the size of organization determines what types of user groups are required. By default Oracle ships with:
- BI Consumer
- BI Author
- BI Administrator
Typically we would recommend inserting the BI Analyst into the default groups:
- BI Consumer
- BI Analyst
- BI Author
- BI Administrator
This works well when there is a central BI team who develop content for the whole organization. The structure would look like this:
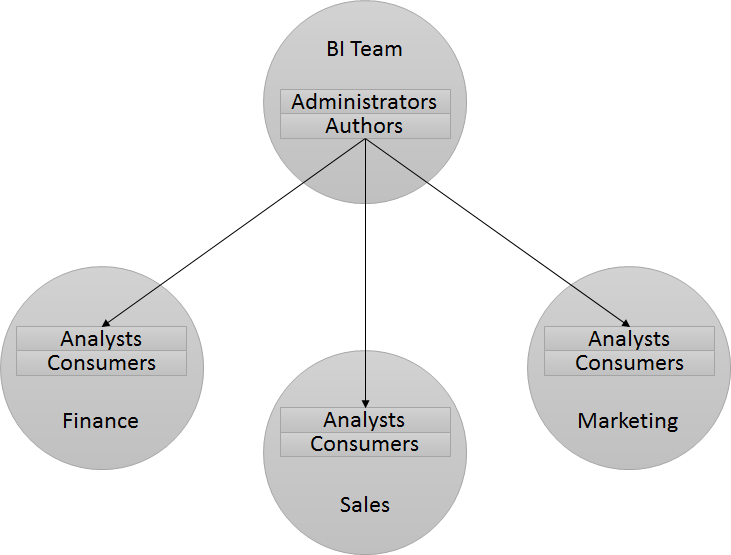
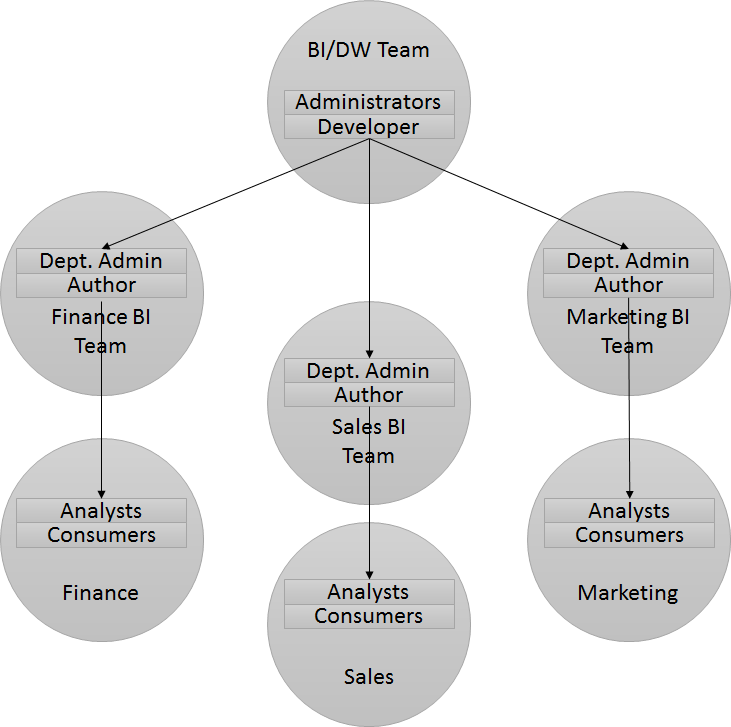
For larger organizations where dashboard development and permissions is handled across multiple BI teams then the BI Department Administrator group can be used to locally manage permissions for each department. Typically we see the BI team as a central Data Warehouse team who deliver the BI model (RPD) to the multiple BI teams. In a large Organization the administration of Oracle BI should be handled by someone who isn't the BI Developer, the structure could look like:
Permissions on groups
Each of the groups will require different permissions, at a high level the permissions would be:
|
Name |
Permissions |
|---|---|
| BI Consumer |
|
| BI Analyst |
|
| BI Author |
|
| BI Department Admin |
|
| BI Developer |
|
| BI Administrator |
|
Understanding the basic security mechanics in 10g and 11g
In Oracle BI 10g the majority of the security is handled in the Oracle BI Server. This would normally be done through initialisation blocks, which would authenticate the user from a LDAP server, then run a query against a database tables to populate the user into ‘Groups’ used in the RPD and ‘Web Groups’ used in the presentation server. These groups would have to match in each level; Database, Oracle BI Server and Oracle BI Presentation Server.
With the addition of Enterprise Manager and Weblogic the security elements in Oracle BI 11g radically changed. Authenticating the user is in the Oracle BI server is no longer the recommended way and is limited in Linux. While the RPD Groups and Presentation Server Web Groups still exist they don’t need to be used. Users are now authenticated against Weblogic. This can be done by using Weblogic’s own users and groups or by plugging it into a choice of LDAP servers. The end result will be Groups and Users that exist in Weblogic. The groups then need to be mapped to Application Roles in Enterprise Manager, which can be seen by the Oracle BI Presentation Services and Oracle BI Server. It is recommended to create a one to one mapping for each group.
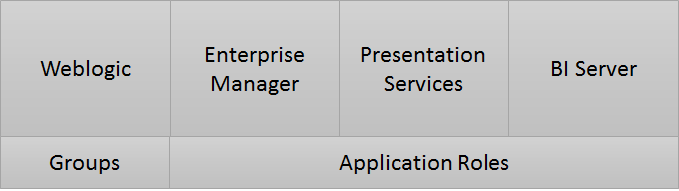
What does all this look like then?
Assuming this is for an SME size organization where the Dashboard development (BI Author) is done by the central BI team the groups would like:
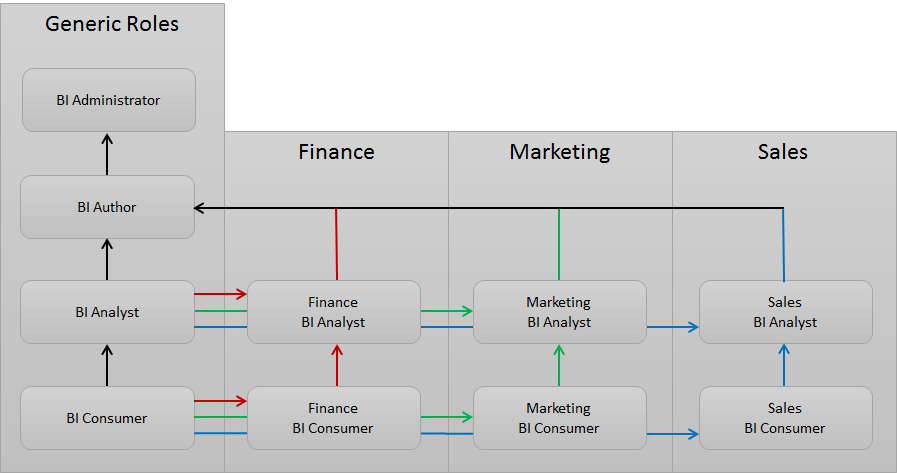
The key points are:
- The generic BI Consumer/Analyst groups give their permissions to the department versions
- No users should be in the generic BI Consumer/Analyst groups
- Only users from the BI team should be in the generic BI Author/Administrator group
- New departments can be easily added
- the lines denote the inheritance of permissions and privileges
Whats next - The Web Catalog?
The setup of the web catalog is very important to ensure that it does not get unwieldy, so it needs to reflect the security model and we would recommend setting up some base folders which look like:
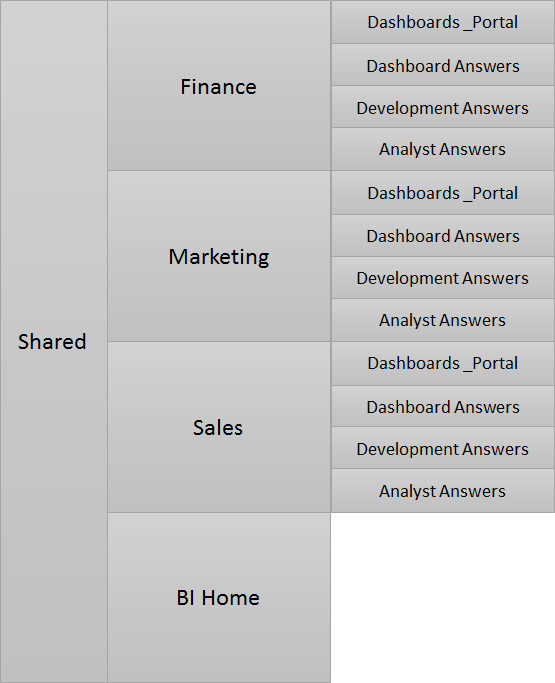
Each department has their own folder and 4 sub folders. The permissions applied to each department’s root folder is BI Administrators so full control is possible across the top. This is also true for every folder below however they will have additional explicit permissions described to ensure that the department cannot create any more than the four sub folders.
- The Dashboard folder is where the dashboards go and the departments BI Developers group will have Full control and the departments BI consumer will have read . This will allow the departments BI Developers to create dashboards, the departments BI Administrators to apply permissions and the departments consumers and analysts the ability to view.
- The same permissions are applied to the Dashboard Answers folder to the same effect.
- The Development Answers folder has Full control given to the departments BI Developers and no access to for the departments BI Analysts or BI Consumers. This folder is mainly for the departments BI Developers to store answers when in the process of development.
- The Analyst folder is where the departments BI Analysts can save Answers. Therefore they will need full control of this folder.
I hope this article gives some insight into Security with Oracle BI. Remember that our Global Services products offer a flexible support model where you can harness our knowledge to deliver your projects in a cost effective manner.